Web3 Security 101: What is the Difference Between Bug Bounties and Audit Contests
This post defines the specific characteristics and optimal use cases of both bug bounties and audit contests.

As the Web3 ecosystem has matured, so have its security practices. Two pillars of a complete security strategy are bug bounties and audit contests. They are often confused with each other, and the two do share the common goal of uncovering vulnerabilities. Besides that, their operational frameworks and strategic applications are distinct. Understanding this distinction is critical for any project architecting its security strategy.
This post will define the specific characteristics and optimal use cases of both bug bounties and audit contests.
Audit Contests
Audit contests are structured as open, time-boxed reviews where security researchers compete to uncover vulnerabilities for rewards.
This model opens the review to hundreds of participants. These participants compete for a pre-defined prize pool based on the severity of submitted findings. Submissions are later triaged, validated, and consolidated into a final report.
Main Benefits of Audit Contests
Audit Contests remain an integral part of the smart contract security process. The strength-in-numbers strategy is becoming a prerequisite for large or complex codebases such as Aave or Ethereum.
- The likelihood of missed bugs is very low because 200-400 security experts try to find bugs in your code.
- Incentives are stronger through competition: experts get paid based on the number of findings and the severity of findings.
- Faster, intense scrutiny in a short window. Contests are usually 7–30 days of hyper-focused review.
- Protocol teams can decide their own prize pool size, making them affordable at any level.
For many security experts, audit contests are the preferred final stress test before launch.
Read more about Sherlock’s industry-leading audit contests here.
Bug Bounties
A bug bounty program is an ongoing, open invitation to security researchers. It is usually deployed after a protocol's core code has been both audited and launched on mainnet. The scope is broader, often encompassing the entire deployed system, including front-end interfaces and infrastructure. Rewards are paid out for valid, unique vulnerabilities based on a public severity matrix. This model provides a persistent security layer, catching issues that emerge from new interactions or upgrades over time.
The Value of Hosting a Bug Bounty
A bug bounty is a pragmatic investment in risk reduction. Instead of hoping your published code survives after launch, you incentivize experts to constantly test its security.
The math is simple: paying a white-hat $25,000 to uncover a vulnerability that could have cost $25 million is a high-return security trade.
Beyond direct protection, a public bounty also builds confidence. It signals to users, partners, and investors that security isn’t just a checkbox; it’s an ongoing commitment.
Sherlock is currently hosting the largest bug bounty of all time in web2 or Web3 for $16,000,000. Read more about Sherlock’s industry-leading bug bounties here.
Where Do Audit Contests and Bug Bounties Fit in the Security Lifecycle?
This is one of the most significant differences between bug bounties and audit contests. Audit contests happen before the code is launched during the auditing phase, and bug bounties are only for code that is already live during the post-launch phase.
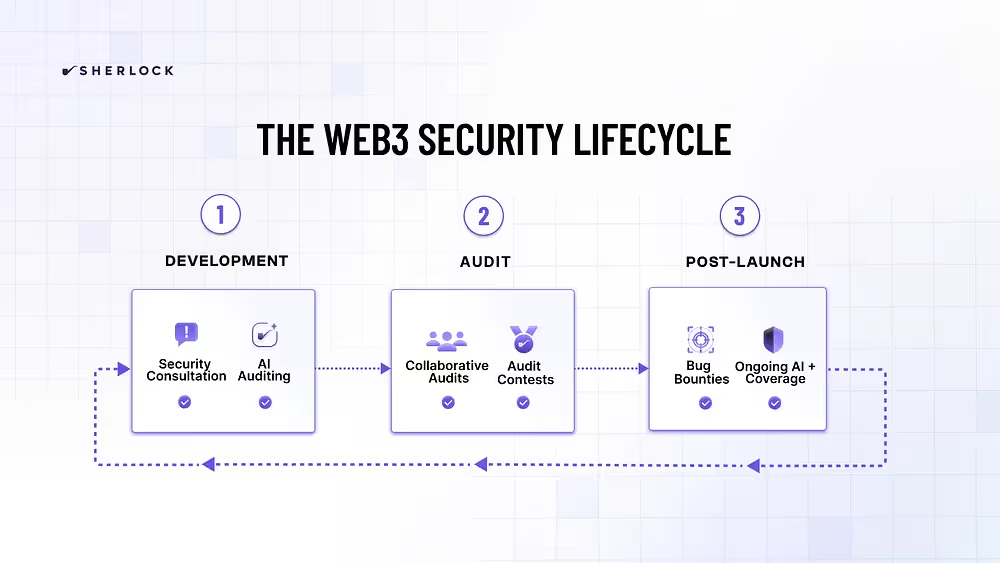
Auditing (Where Audit Contests Happen)
The development focus turns to intense adversarial scrutiny. Teams engage external audit firms, conduct coordinated reviews, or launch contests that bring far more eyes and far more inventive thinking to the code. This is the phase where you specifically want reviewers breaking assumptions, chaining together unlikely execution paths, and thinking like hostile attackers instead of like the original authors.
Post-Launch (Where Bug Bounties Happen)
The protocol finally faces reality. Genuine liquidity moves through it. Other contracts integrate with it. This stage demands active monitoring, well-structured bug bounties, prepared incident response, and sometimes difficult calls on upgrades, migrations, or emergency pauses.
Core Differences Between Bug Bounties and Audit Contests
Timing
Audit contests are a discrete, pre-deployment event. Bug bounties are a continuous, post-deployment program.
Scope
Contests target a specific snapshot of code, usually core smart contracts. Bounties have a broader scope, often including the entire live system and its front-end.
Reward Structure
Audit contests feature a large, consolidated prize pool for findings made during a short period. Bug bounties offer variable, per-find rewards based on severity, paid out indefinitely.
Strategic Role
An audit contest serves as a foundational security review before launch. A bug bounty provides ongoing vigilance in production.
Maturity Model
A comprehensive security strategy employs both sequentially: an audit contest first, followed by a sustained bug bounty.
FAQ
Q: Which should a new project do first?
A: An audit contest is almost always the first step. It is used to secure the core code before launch. However, audit contests are not the first step of a complete security strategy.
Q: Can findings from a bug bounty be made public?
A: This depends on the program's policy. Many programs allow for private disclosure, with possible public release after a fix is deployed.
Q: What is a bug bounty contest?
A: It is an audit contest without a guaranteed rewards pool. Rewards are only payed out if vulnerabilities of a set severity are found.
Q: How are reward levels determined?
A: Audit contest rewards are set by the prize pool. Bug bounty rewards follow a published severity matrix. Both audit contest rewards pools and bug bounty rewards are set by the protocol team.
Q: Is one model more cost-effective than the other?
A: Not directly comparable. Audit contests are a defined capital outlay for deep review. Bug bounties are a continuous cost of operation, paying only for valid results. Both are investments in risk mitigation.