Centrifuge x Sherlock AI: Continuous Security in the Development Workflow
Centrifuge integrated Sherlock AI into daily development and audits to surface earlier security signal across a complex, multi-chain protocol and reduce late-stage risk.

Centrifuge is a leading Web3 protocol building core infrastructure for on-chain asset management. They enable teams to tokenize and distribute financial products across multiple blockchains using immutable smart contracts and standards-based vaults. Its design supports a wide range of use cases, from permissioned funds to onchain lending and custom financial structures, all operating within a hub-and-spoke, multi-chain model.
That flexibility introduces meaningful complexity. Centrifuge is live across six blockchains, combines an immutable core with modular extensions, and coordinates accounting, pricing, and liquidity across networks. In systems like this, development-time changes can affect multiple interacting contracts at once, increasing the cost of discovering issues late.
To get earlier security signal during development, the Centrifuge team adopted Sherlock AI and integrated it into their workflow alongside formal reviews. This case study looks at how Centrifuge uses Sherlock AI in practice and how it fits into their approach to preparing code for audits and production.
Security needs that lead to Centrifuge adopting Sherlock AI
Before Sherlock AI, Centrifuge relied primarily on scheduled point-in-time security reviews to evaluate deeper system behavior. While this approach is industry standard and effective for major milestones, it can offer less visibility during periods of active development and early auditing, when changes are frequent and interconnected.
Centrifuge’s protocol design makes early visibility of potential security problems especially important. The system spans multiple blockchains, uses a hub-and-spoke model for control and accounting, and combines an immutable core with modular extensions. In architectures like this, incremental changes can interact in subtle ways, increasing the cost and associated problems of discovering vulnerabilities and security issues too late in the process.
Why earlier security signal matters in systems like Centrifuge’s
Cross-chain coordination and state synchronization
Centrifuge's hub chain manages accounting and pricing while spoke chains handle token distribution across six networks. A vulnerability in hub logic that affects state synchronization means fixes must cascade across all deployed networks, each requiring separate testing and deployment - work that's straightforward during development but chaotic when discovered during audit under compressed timelines.
Extension interactions with the immutable core
The protocol combines an immutable core with modular extensions for compliance, allocation, pricing, and cross-chain behavior. An extension that passes isolated review can still break when combined with other extensions or when core contract state changes, and validating those interactions becomes exponentially more complex as extensions are added - issues caught during development get fixed before interaction paths multiply.
Delayed fixes expand blast radius
In a multi-chain system with shared hub logic, issues discovered late often sit beneath multiple layers of dependent code. By the time an audit surfaces a problem, new spokes, adapters, or extensions may already rely on the affected behavior. Fixing it then requires untangling downstream dependencies rather than making a localized change, increasing both risk and remediation time.
How Centrifuge utilizes Sherlock AI
Centrifuge used Sherlock AI in two complementary modes: incremental analysis on pull requests and broader analysis on the full codebase. Each served a different purpose within the development workflow.
Pull request scans
For pull requests, Sherlock AI analyzed only the changes introduced in each PR and how those changes interacted with the existing codebase. This allowed the system to surface issues tied directly to new logic, permission changes, or altered control paths as code was introduced.
During these PR scans, Sherlock AI identified two medium-severity issues, which were reviewed and addressed while the surrounding code changes were still fresh and easy to reason about.
Full codebase runs
In addition to incremental PR checks, the team ran Sherlock AI against the full codebase on the main branch to get broader system-level coverage when preparing for deeper reviews.
Full codebase runs surfaced:
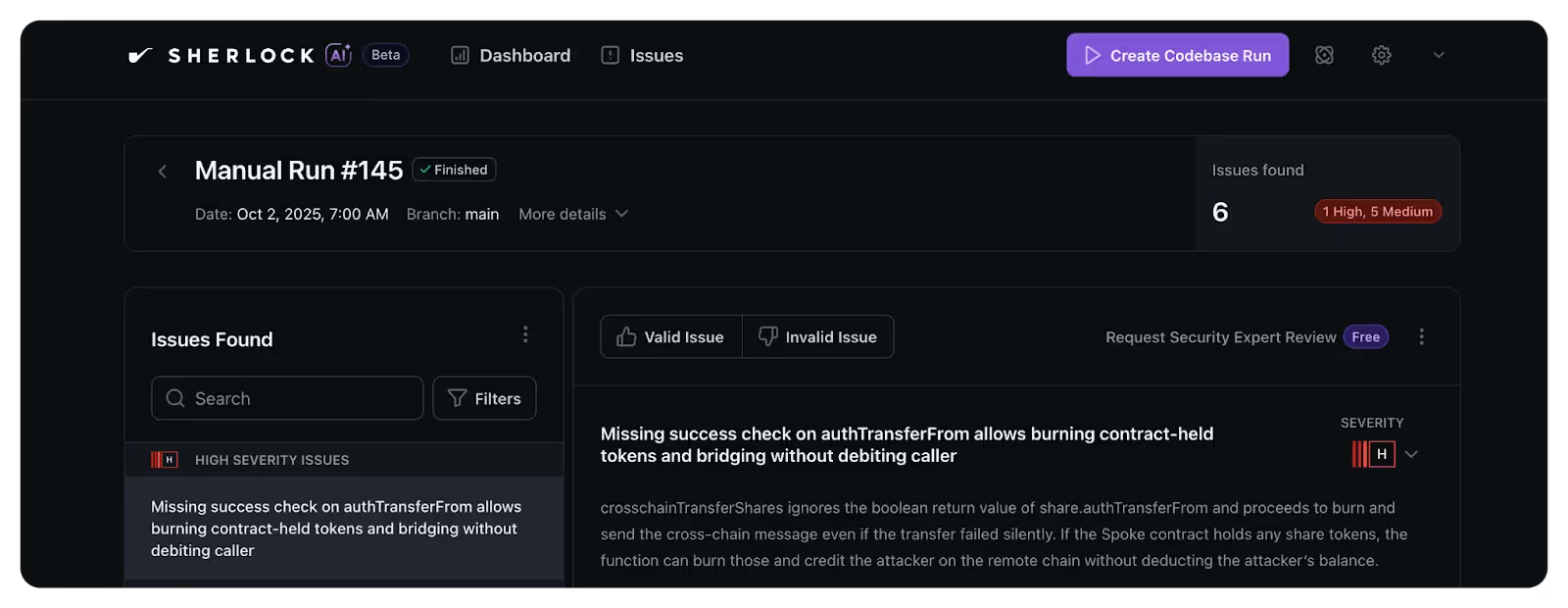
- 1 high-severity issue
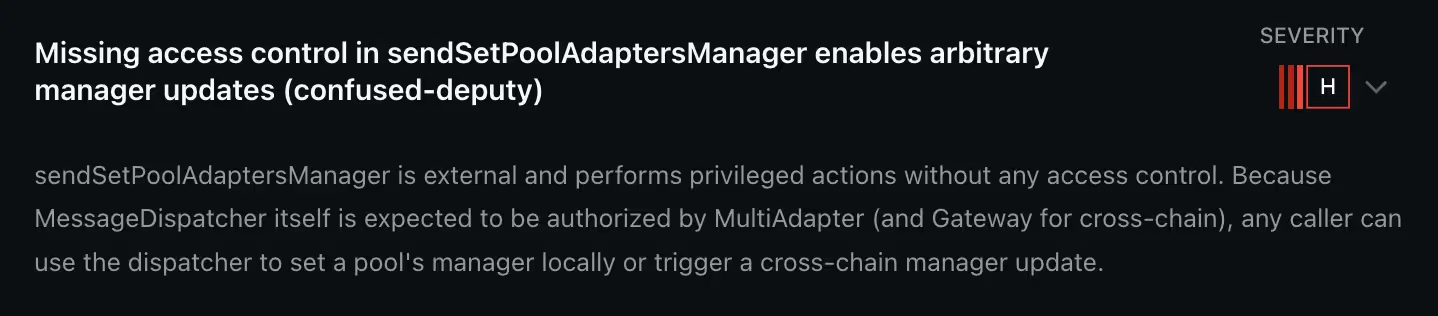
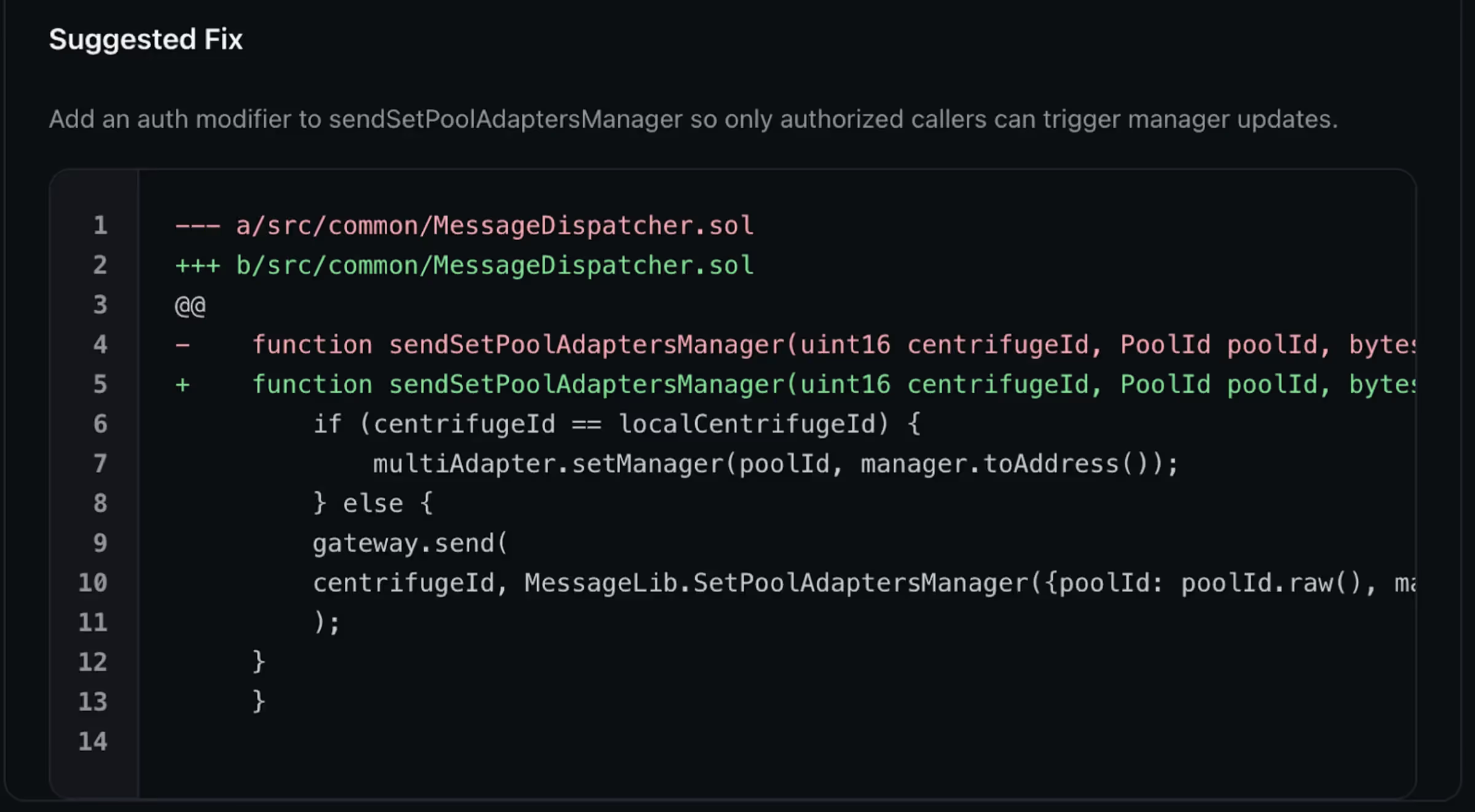
- This High vulnerability was a Missing Access Control bug:
Because sendSetPoolAdaptersManager lacked access control, any user could hijack it to set themselves as a pool’s manager (locally or cross-chain) gaining unauthorized control over adapter management.
- This High vulnerability was a Missing Access Control bug:
- 3 medium-severity issues across broader system interactions.
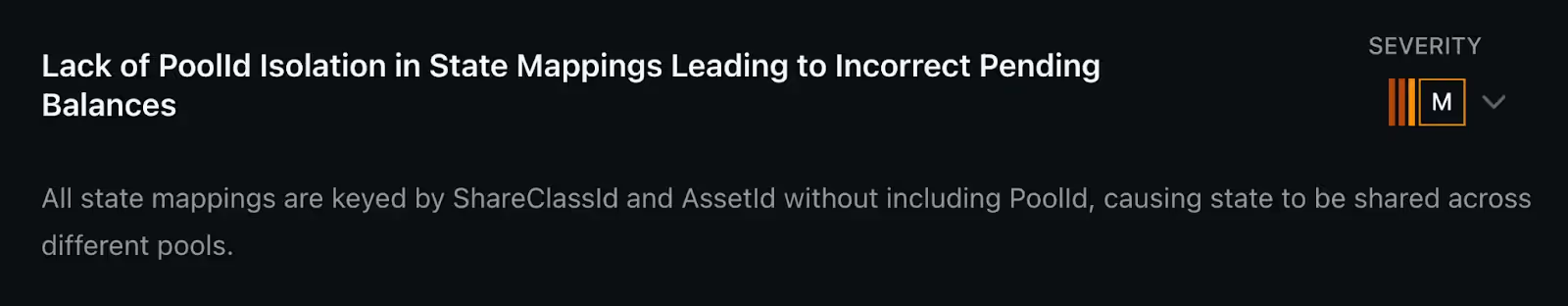
- One Medium vulnerability was a state isolation bug that caused shared pending balances and incorrect deposits or redemptions across pools. The fix required keying all mappings and epochs by PoolId.
This combination of incremental and holistic analysis allowed the team to move between day-to-day development and higher-level review using the same tooling, without switching workflows.
Fix Review: Triage and remediation
Sherlock AI helped identify the root causes behind findings and provided guidance on remediation. Those findings were handled as part of Centrifuge’s normal development workflow rather than treated as separate security output.
Results were visible to multiple developers at once, allowing issues to be reviewed in shared context and resolved without duplicated effort. After fixes were applied, analysis was re-run to confirm remediation before changes moved forward.
- Shared visibility: Issues were triaged once and reviewed collaboratively rather than in parallel by multiple contributors.
- Verification after fixes: Re-running analysis confirmed remediation before changes moved forward.
This kept security review tightly coupled to code changes and prevented findings from accumulating into late-stage remediation work.
Use During The Auditing Process
Sherlock AI continued to be used during formal audit phases, where it served as an additional source of signal alongside human review rather than a replacement for it. During the audit contest, Sherlock AI surfaced two medium-severity issues, complementing findings from researchers and helping maintain visibility as multiple review paths ran in parallel. This allowed the team to carry the same security workflow and context from development into auditing, keeping analysis and review continuous rather than resetting processes at each phase.
Results and impact
Using Sherlock AI in daily development shifted security work earlier, reducing unresolved issues as code was written and improving visibility as the system evolved. By the time formal reviews began, most fixes were already handled in flow, which cut down rework and context switching for engineers. Review time focused less on basic issues and more on deeper system behavior, strengthening confidence in both the process and the outcome.
- Faster & better informed decisions during development: Continuous scanning surfaced security signal earlier in the workflow, letting the team prioritize fixes sooner and avoid carrying ambiguous risk into later phases.
- Developer time saved during audits: Fewer late discoveries reduced rework and context switching, saving engineering hours during formal review phases.
- Lower audit overhead and burn: Cleaner code entering audits shortened remediation cycles and reduced the cost of extended audit timelines.
Closing: Giving Teams Leverage Throughout the Lifecycle
Centrifuge’s experience shows how continuous security analysis can sit naturally inside an advanced protocol’s development process. By running Sherlock AI throughout day-to-day engineering and into formal audits, the team kept security signal close to where decisions were being made, while code context was still intact and fixes were straightforward to apply.
Rather than treating security as a late checkpoint, Centrifuge carried a single, consistent workflow from development through audit readiness. That continuity helped the protocol reach audits in a stronger state and allowed human reviewers to focus on deeper system behavior, reinforcing Centrifuge’s broader approach to building and operating complex, multi-chain infrastructure with discipline and clarity.
“I’ve tried many different AI audit tools, and none come even close to Sherlock AI. It combines best-in-class AI models with easy-to-use UX and GitHub integration. Other tools are either good at PR runs or manual runs. Sherlock AI is by far the best combination of both.”
— Jeroen Offerijns, Co-Founder & CTO, Centrifuge Labs


