What Is A CISO In Web3?
In the evolving landscape of Web3, a Chief Information Security Officer (CISO) serves as the cornerstone of robust security strategies, safeguarding decentralized protocols, DeFi platforms, and NFT ecosystems from sophisticated threats while enabling innovation and compliance.

In the evolving landscape of Web3 and blockchain technology, a Chief Information Security Officer (CISO) serves as the cornerstone of robust security strategies, safeguarding decentralized protocols, DeFi platforms, and NFT ecosystems from sophisticated threats while enabling innovation and compliance.
While they are common at more established web2 companies, they are not yet commonplace in Web3. A traditional CISO is responsible for protecting the organization’s data, systems, and users by defining security strategy, managing cyber risk, and ensuring compliance with regulations.
However, in Web3, the role expands to address the decentralized, transparent, and often pseudonymous nature of blockchain protocols. Here, a CISO must safeguard not just centralized servers but also smart contracts, wallets, on-chain assets, and the broader ecosystem against exploits. As the protocol scales, security decisions move beyond engineering hygiene and become leadership decisions that affect trust, growth, and survival.
This is where the role of a Web3 CISO becomes critical.
Key CISO Functions and Responsibilities in Web3
Web3 security assumes adversaries are sophisticated, well-capitalized, and continuously monitoring the system. There is no perimeter to defend and no reliable rollback once something breaks. The CISO exists to make sure the protocol is designed and operated with these constraints in mind.
A Web3 CISO is accountable for:
- Protocol-Level Threat Modeling
- Smart Contract Security Oversight
- Incident Response and Exploit Readiness
- Key Management and Operational Security
- Security Programs and Researcher Engagement
1. Protocol-Level Threat Modeling
A Web3 CISO is responsible for understanding how a protocol can realistically fail under adversarial conditions. This involves analyzing smart contract invariants, economic assumptions, oracle dependencies, governance mechanics, upgrade paths, and composability risks. The goal is to identify which failure modes are survivable and which ones represent existential threats to the protocol.
2. Smart Contract Security Oversight
A Web3 CISO oversees smart contract security across the full development lifecycle rather than treating audits as a one-time checkmark. This includes shaping architecture decisions, coordinating audits and reviews, ensuring findings are correctly remediated, and evaluating tradeoffs around immutability, upgradeability, and emergency controls. The focus is on reducing systemic risk rather than eliminating individual bugs.
3. Incident Response and Exploit Readiness
A Web3 CISO ensures the protocol is prepared to respond effectively when something goes wrong. This means defining who can act in an emergency, how damage can be limited on-chain, how communication is handled, and how to work with researchers and recovery partners. Preparation and clarity are critical to preventing an incident from escalating into a protocol-ending event.
4. Key Management and Operational Security
A Web3 CISO is responsible for protecting the keys and access paths that control the protocol. This includes designing multisig architectures, setting signer policies, enforcing hardware wallet usage, managing access to infrastructure, and establishing operational security standards for contributors. Many of the largest losses in Web3 stem from failures in this area rather than from contract bugs.
5. Security Programs and Researcher Engagement
A Web3 CISO designs and runs ongoing security programs that engage external researchers as part of the protocol’s defense. This includes structuring bug bounties, defining disclosure processes, coordinating fixes, and feeding lessons from reports back into protocol design. Over time, this creates a continuous feedback loop that strengthens the system as it evolves.
Does Your Protocol Need a CISO? Key Signals
A protocol usually needs a CISO once security decisions stop being straightforward. If you’re struggling with the question, you should likely consider the role.
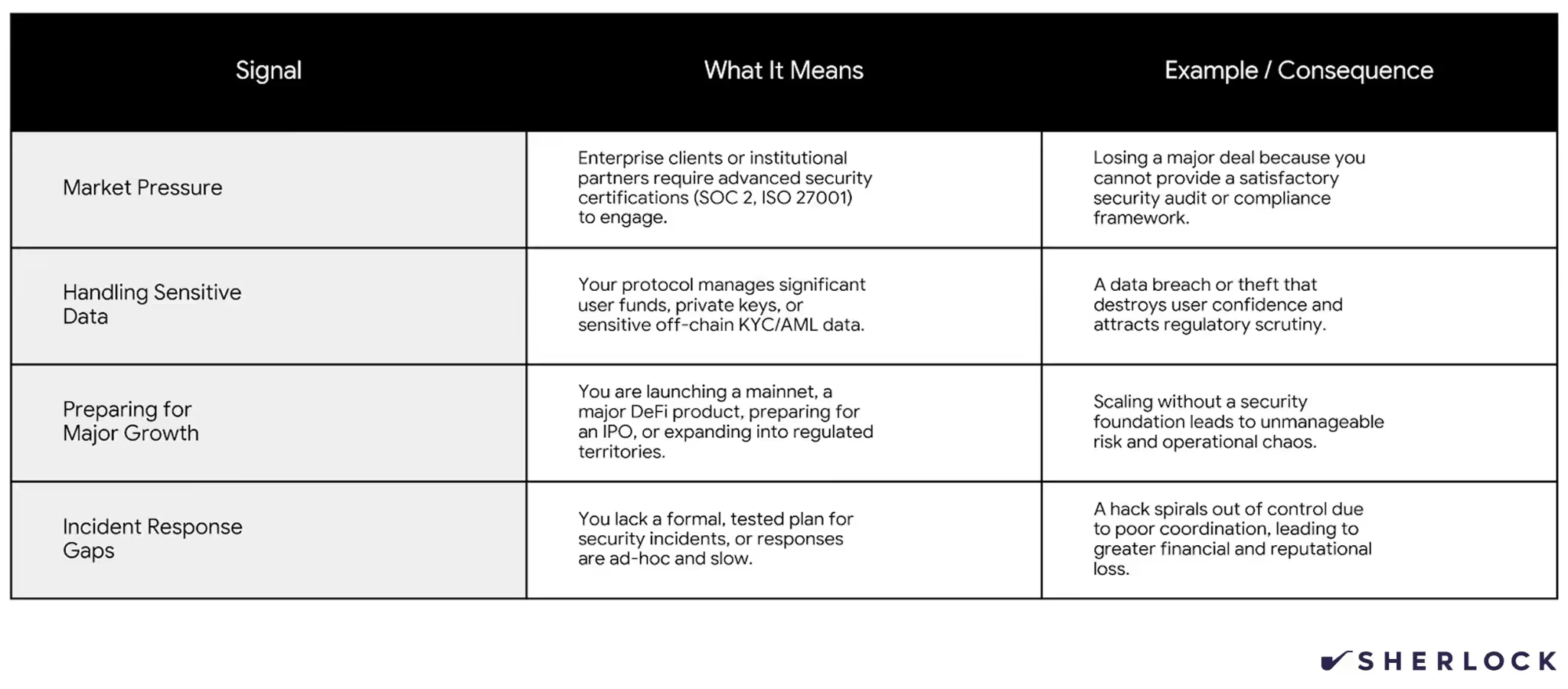
When a Web3 CISO Creates Clear Value
DeFi Protocols with Meaningful TVL
As TVL grows, the impact of a single exploit increases dramatically. Economic attacks, upgrade risks, and composability failures become more likely. A CISO helps founders reason about tradeoffs between shipping quickly and preserving long-term trust.
DAOs and Foundations Managing Large Treasuries
Treasury security introduces governance risk, signer exposure, and social engineering threats. A CISO helps design systems that balance decentralization with operational safety.
Infrastructure, Bridge, and Cross-Chain Protocols
These systems concentrate risk and attract sophisticated attackers. Failures often propagate across ecosystems. Dedicated security leadership is often necessary for long-term viability.
How Sherlock Can Help
Sherlock does not provide CISOs as a primary service, but we work closely with protocols that are building mature security organizations. We help teams define a complete security strategy by identifying their highest-risk areas, designing appropriate security programs, and aligning audits, bug bounties, and incident readiness around real threats rather than checklists.
For protocols that are approaching the stage where dedicated security leadership makes sense, Sherlock can also help founders understand what to look for in a Web3 CISO and facilitate introductions to experienced security leaders. Our goal is to help teams move from reactive security decisions to a clear, intentional approach that scales with the protocol.
Final Thoughts
In Web3, security directly determines whether a protocol earns and keeps user trust. A Web3 CISO exists to ensure security decisions are deliberate, informed, and aligned with the protocol’s goals as it scales.
90% of Web3 organizations lack dedicated security roles, making them prime targets. Investing in a CISO can prevent catastrophic losses and build user trust.
The teams that invest in security leadership early tend to survive long enough to matter.
FAQ: CISOs in Web3
Do audits replace the need for a CISO?
No. Audits review code at a specific point in time. A CISO manages security risk across the protocol’s entire lifecycle.
Is security just the responsibility of engineers?
Engineers implement security controls. A CISO decides how much risk the protocol is willing to accept and where resources should be allocated.
Is it too early to think about a CISO before launch?
It is rarely too early to define security ownership. It can be too early to hire full-time, but not to plan.
Can a DAO have a CISO?
Yes. Many DAOs appoint a security lead, committee, or contracted CISO to coordinate risk management and incident response.
What is the most common security mistake in Web3?
Treating security as a checklist instead of an ongoing, adversarial process.