Morpho Vaults V2: Blackthorn Audit for an Immutable Vault Standard
Morpho Vaults V2 is a universal gateway to onchain yield. Sherlock and Blackthorn pressure-tested the system, helping Morpho ship Vaults V2 securely ahead of its September 2025 launch.

About Morpho
Morpho is lending infrastructure for onchain capital. It connects lenders and borrowers to optimal opportunities, and it is designed to be embedded, allowing enterprises, institutions, and applications to offer lending and borrowing products directly within their own platforms.
At the protocol level, Morpho is built in two layers.
Morpho Markets are immutable, configurable lending markets. Morpho Vaults sit above them as programmable, noncustodial model portfolios that allocate across markets, enabling depositors to earn yield through curated strategies while retaining the ability to exit at any time.
This architecture positions Morpho as more than an end-user product. It is a capital routing layer that other teams build on. When infrastructure becomes composable at this level, security becomes a foundational requirement. Teams rely on Morpho as a base layer, which places the security bar firmly at an infrastructure standard from day one.
What Vaults V2 Changes
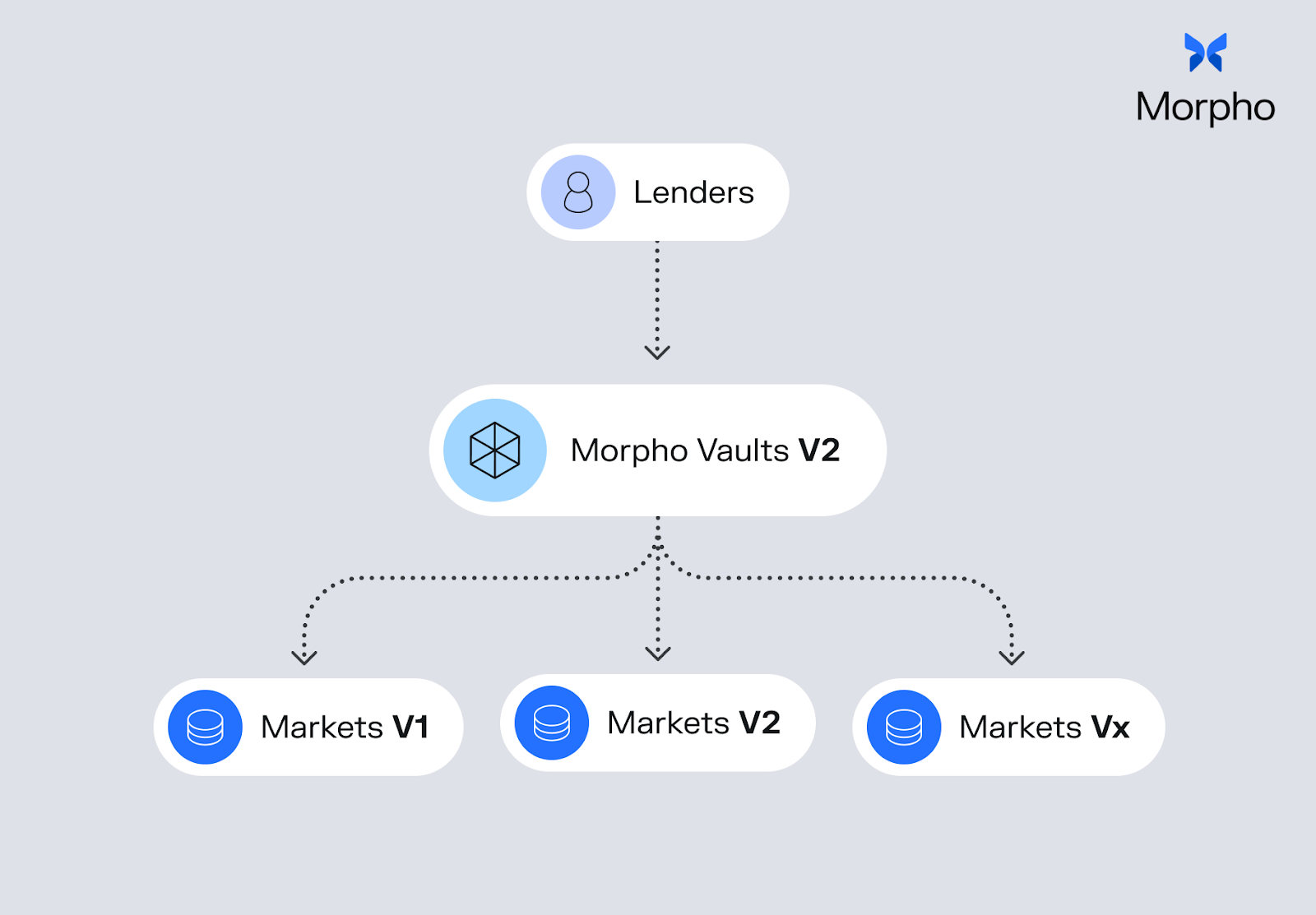
Vaults V2 is a universal gateway to onchain yield, enabling vaults to allocate assets across Morpho V1, Morpho V2, and future Morpho protocols. Vaults generate yield for depositors by allocating across protocols, while a revamped role system governs how capital is managed under explicit constraints.
Vaults V2 introduces greater flexibility through multiple roles with distinct powers, granular risk controls including absolute and relative caps to manage exposure across collateral assets and other factors, and configurable controls around deposits and withdrawals. Together, these design choices increase the number of edge cases around permissions, accounting, and exit behavior that must be handled correctly.
Because Vaults V2 is intended to serve as long-lived infrastructure, pre-deployment review was the primary opportunity to validate how these interactions behave before they were relied on in production.
Security Goals And Threat Model
For Vaults V2, the goal was to prove that the system behaves correctly under adversarial conditions. That meant validating behavior under transaction sequencing, role misconfiguration, stressed liquidity, and complex market states rather than focusing on isolated defects.
The highest-risk failure modes fell into three areas:
- Permission boundaries where allocator or curator actions could push the vault into unsafe configurations.
- Accounting and timing behavior where share price, total assets, or redemptions could be influenced by multi-step transactions.
- Adapter integrations where the vault routes capital to underlying protocols and must correctly handle allocation, deallocation, and asset accounting as markets are added or removed
Morpho’s bar was to ship a vault standard that enterprises could rely on as infrastructure. The audit focused on pressure testing the system where it bends: role actions, caps, allocations, withdrawals, and redemptions, treating Vaults V2 as a living system rather than a static contract set.
Why Sherlock And Blackthorn
Sherlock’s collaborative auditing model is built around dynamic team assembly. Instead of relying on fixed audit rosters, each engagement is staffed from an elite researcher network whose members have demonstrated performance across live audits, contests, and bug bounties. That performance history allows Sherlock to match researchers to the specific architecture being reviewed, so the audit team reflects the system itself rather than availability.
That approach mattered for Vaults V2. This was a configurable vault framework with multiple roles, adapters, and exit paths, designed to remain immutable and operate as long-lived infrastructure. Systems like this demand auditors who can reason about how state, permissions, and capital flows behave under adversarial sequencing, role misconfiguration, and stressed liquidity, and who can surface issues that only appear when legitimate actions are composed in unexpected ways.
That’s why Sherlock brought in Blackthorn. Blackthorn is Sherlock's most elite tier of auditors, reserved for protocols building critical infrastructure that require the network's most experienced security researchers. Vaults V2 met that bar, so the engagement was led by Blackthorn researchers who could engage immediately with vault accounting, market interactions, and role-based controls, and deliver depth without sacrificing launch velocity.
How The Team Was Assembled And How The Engagement Ran
Sherlock staffed the engagement with four senior researchers from Blackthorn, chosen for demonstrated performance on complex financial systems and consistent judgment under adversarial conditions. The engagement was run as an architecture-first collaborative audit, focused on understanding the vault as a system and tracing how capital moves across roles, adapters, and state transitions.
Simao — Led the review and coordinated system-level analysis across the Vaults V2 architecture. Simao is ranked 2nd on Sherlock’s all-time leaderboard, a founding member of Blackthorn, and Sherlock’s 2025 Watson of the Year.
hyh — Reviewed core vault behavior with attention to correctness under adversarial sequencing and real usage patterns. Hyh placed 3rd in the Morpho Blue Audit and is a founding member of Blackthorn.
pkqs90 — Focused on configuration and adapter risk, including curator and allocator actions that could create unintended outcomes. Pkqs90 is also a founding member of Blackthorn.
xiaoming90 — Reviewed withdrawal and redemption paths, with emphasis on edge cases affecting user exits and vault liveness. Xiaoming90 is also a founding member of Blackthorn.
The audit followed a tight loop: identify issues that emerge when legitimate actions are composed, then validate fixes against the same adversarial reasoning that surfaced them. The result was not just a list of findings, but a clearer set of constraints around how Vaults V2 behaves under stress and integration.
Outcomes And What Morpho Shipped
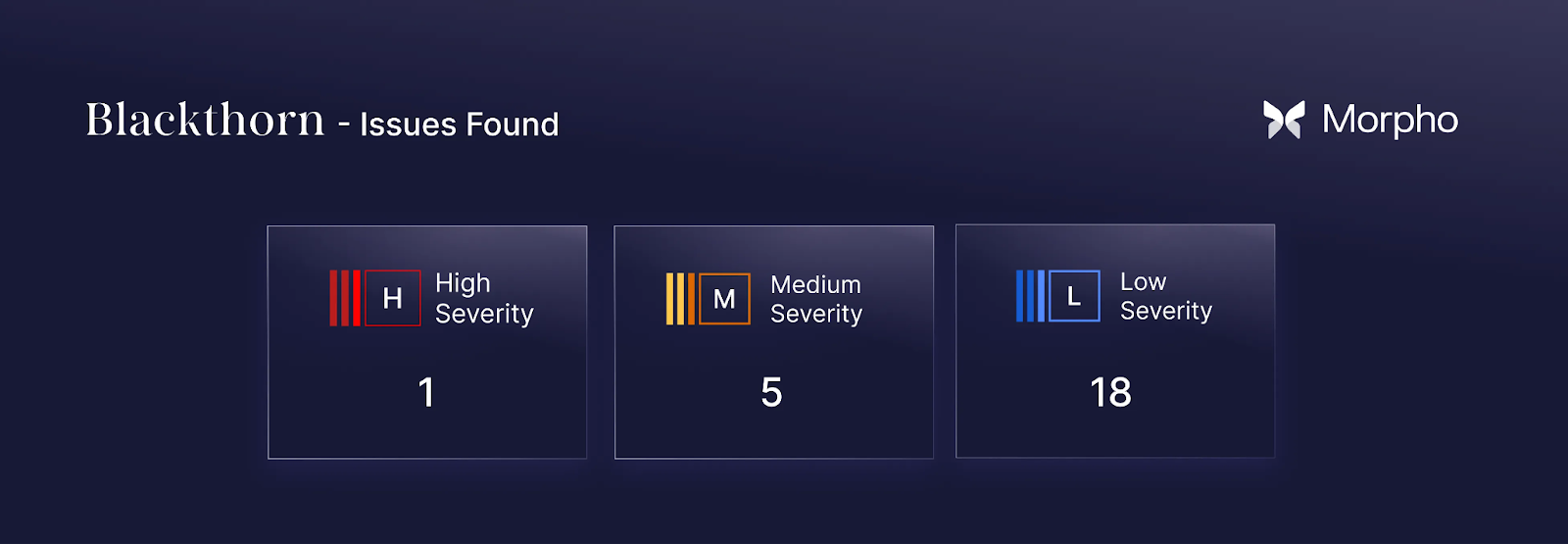
By the time Blackthorn began its review, Morpho had already invested heavily in security, including multiple audits from tier-1 firms. Because the codebase was evolving quickly during earlier reviews, Morpho brought in Blackthorn for an additional round of auditing. Blackthorn scoped its engagement around system behavior under adversarial conditions rather than broad surface coverage. Within seven days, the team delivered 24 findings across Vaults V2, including 1 High and 5 Medium, centered on adversarial sequencing, stressed liquidity, and complex role interactions.
The High severity issue revealed a vault-specific exploit path where transaction-level accounting allowed a sophisticated actor to exit at a favorable share price while shifting bad debt onto remaining depositors. This was not a faulty check or an isolated logic error. It required reasoning across accounting snapshots, liquidation timing, and atomic execution, the kind of behavior that only emerges when legitimate actions are composed adversarially.
Audit results at a glance:
- 1 High severity issue
Vault accounting behavior that enabled loss avoidance through transaction sequencing and socialized bad-debt impact. - 5 Medium severity issues
Edge cases affecting user safety and fairness, including withdrawal and redemption slippage exposure, adapter disablement timing risks, blocked deposits under certain cap configurations, fee-related loss scenarios, and delayed-yield extraction. - 18 Low / Informational issues
Documentation updates and behavioral clarifications that improved operator and integrator understanding of Vaults V2.
Taken together, the audit produced concrete findings that the Morpho team addressed leading into launch. Issues were resolved in the codebase and reviewed during a formal fix review period, where Blackthorn researchers verified that the remediations closed the findings without introducing any new issues. With that process complete and the final commit signed off, Vaults V2 shipped shortly after on September 30, 2025, meeting the security standard expected of immutable infrastructure.


