What is Formal Verification?
What is Formal Verification, and What Role Does It Play in Smart Contract Auditing? This post details the methodology, tools, and practical application of Formal Verification in a smart contract audit.

Smart contract security often operates on probability. Auditors hunt for bugs, fuzzing tools bombard contracts with random inputs, and the final report concludes that no critical issues were found. But in a domain managing billions in value, "not found" is not the same as "non-existent." Formal Verification (FV) challenges this probabilistic model, aiming to replace it with mathematical certainty for a contract's most critical properties.
This post details the methodology, tools, and practical application of Formal Verification in a smart contract audit.

Formal Verification is the process of using formal methods to mathematically prove the correctness of a system relative to a defined specification. For smart contracts, this involves three core components:
1. Formal Specification
2. Formal Mathematical Model
3. Verification Tool (Prover)
1. Creating a Formal Specification
The specification is the single source of truth. It is a precise, unambiguous description of the system's desired behavior, written in a formal language. A poor specification renders the entire process useless. Specifications typically define two types of properties:
Safety/Invariant Properties: Conditions that must always hold. These are often security-critical.
- Example: totalSupply() == sum_of_all_balances. (Conservation of tokens).
Liveness Properties: Conditions that must eventually be true.
- Example: A user-initiated withdrawal request will eventually be fulfilled.
2. Translating the Code into a Mathematical Model
The smart contract code and the EVM state are translated into a mathematical model. This model represents the system as a state machine, where transactions cause state transitions. The prover reasons about all possible states and transitions.
3. Running the Proof
Dedicated FV tools analyze the formal model against the specification. They use techniques like theorem proving and model checking. Theorem proving constructs a mathematical proof of correctness step-by-step, often requiring expert guidance. Model checking exhaustively explores all possible state transitions to verify that the specification holds.
If the proof succeeds, you have a high degree of certainty that the code is correct relative to its spec.
If the proof is violated, the tool generates a counterexample. This counterexample is a precise sequence of transactions and inputs that breaks the invariant. This is one of FV's most powerful features for debugging.
Formal Verification in the Auditing Process
Formal Verification is not a replacement for other audit techniques but a complementary, deep-analysis phase. Its integration into an audit workflow is methodical.
When a proof fails, the generated counterexample is analyzed. The outcome is either:
A True Positive Bug: The counterexample reveals a genuine flaw in the logic (e.g., a reentrancy vulnerability, an arithmetic error).
A False Positive: The specification was too strict or did not account for a valid program state, requiring the spec to be refined.
The final deliverable includes not only a list of discovered bugs but also a list of mathematically proven properties. This provides a higher level of assurance for the protocol and its user
Smart Contract Formal Verification Tools
- Halmos
- a16z developed this bounded symbolic execution tool. It integrates seamlessly with Foundry, uses assertions or properties in Solidity, and explores execution paths symbolically to find violations or prove the absence in bounded scenarios.
- a16z developed this bounded symbolic execution tool. It integrates seamlessly with Foundry, uses assertions or properties in Solidity, and explores execution paths symbolically to find violations or prove the absence in bounded scenarios.
- Certora Prover
- Certora applies SMT-based constrained solving and automated verification to prove properties written in CVL (Certora Verification Language). It analyzes bytecode directly and checks functional correctness, invariants, and security properties exhaustively.
- Certora applies SMT-based constrained solving and automated verification to prove properties written in CVL (Certora Verification Language). It analyzes bytecode directly and checks functional correctness, invariants, and security properties exhaustively.
- Act/K Framework
- Runtime Verification created Act as a specification tool with multiple backends (SMT, Coq, hevm, KEVM). Kontrol serves as its modern Foundry-native version, turning tests into proofs using formal semantics.
The Strengths and The Limits of Formal Verification
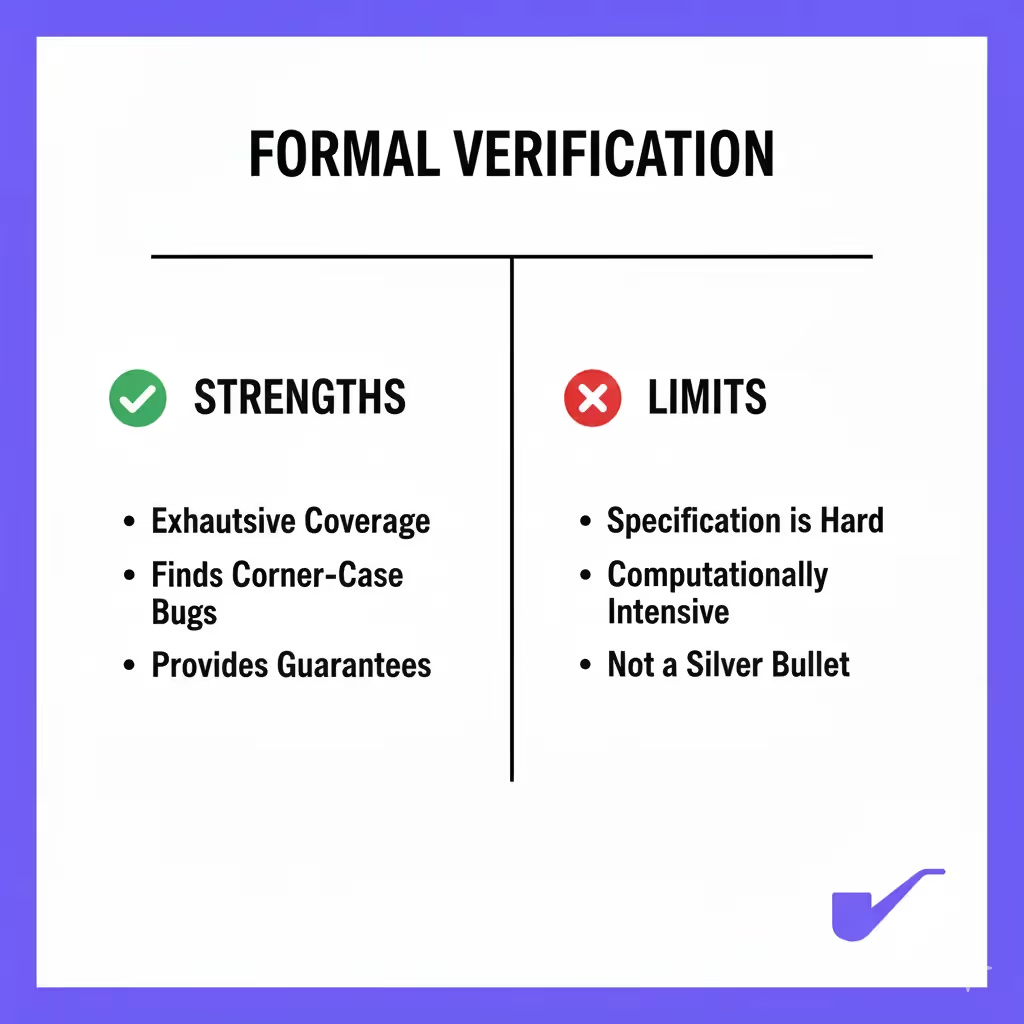
Strengths:
- Exhaustive Coverage: It considers all possible execution paths and inputs, not just a sample.
- Finds Corner-Case Bugs: It excels at discovering complex, multi-transaction vulnerabilities that are nearly impossible to find manually or through fuzzing alone.
- Provides Guarantees: It moves security from probabilistic ("we're pretty sure") to deterministic ("we know for a fact") for the properties verified.
Limits:
- Specification is Hard: Writing correct and complete specifications is difficult and requires deep expertise. Garbage in, garbage out.
- Computationally Intensive: For very complex contracts, the proofs can be time-consuming or even intractable.
- Not a Silver Bullet: FV only proves that the code matches the spec. It cannot prove that the spec itself is correct or captures all desired business logic. A flawed spec can lead to a "verified" but functionally wrong contract.
Conclusion
Formal Verification provides a rigorous, mathematical approach to verifying specific properties of smart contracts. By applying formal methods to core security invariants, it can offer deterministic proofs where traditional testing only provides probabilistic assurance.
Ultimately, Formal Verification shifts the security dialogue from "we did not find vulnerabilities" to "we have proven that these specific vulnerabilities cannot exist within the defined parameters." This makes it a powerful tool for enhancing trust in smart contract code, though it does not eliminate the need for other audit techniques or guarantee overall system correctness. Formal Verification is a complementary layer in a comprehensive security strategy.
If you are looking for a full-stack Web3 security partner to help you secure your smart contract code, contact Sherlock today to learn about our lifecycle security model.


