Top Web3 Security Threats: OpSec Best Practices for 2026
Operational security is more important than ever before as attacks become faster and more sophisticated every day.This guide outlines the critical security threats emerging for 2026 and provides actionable, no-nonsense OpSec best practices to help you stay ahead of adversaries.

The Web3 security landscape is evolving at an increasing pace with the emergence of AI. While the promise of self-custody is empowering, it demands unprecedented personal responsibility. The threats aren't just technical; they are psychological, social, and systemic.
As leaders in Web3 security at Sherlock, we've secured over $100B in TVL and identified more than 1,500 critical vulnerabilities. In 2025, Web3 suffered $3.4B in losses from hacks, with major incidents like the $1.5B Bybit breach highlighting gaps in operational security.
Operational security is more important than ever before as attacks become faster and more sophisticated every day.
This guide outlines the critical security threats emerging for 2026 and provides actionable, no-nonsense OpSec best practices to help you stay ahead of adversaries.
What OpSec Means in Web3 Security
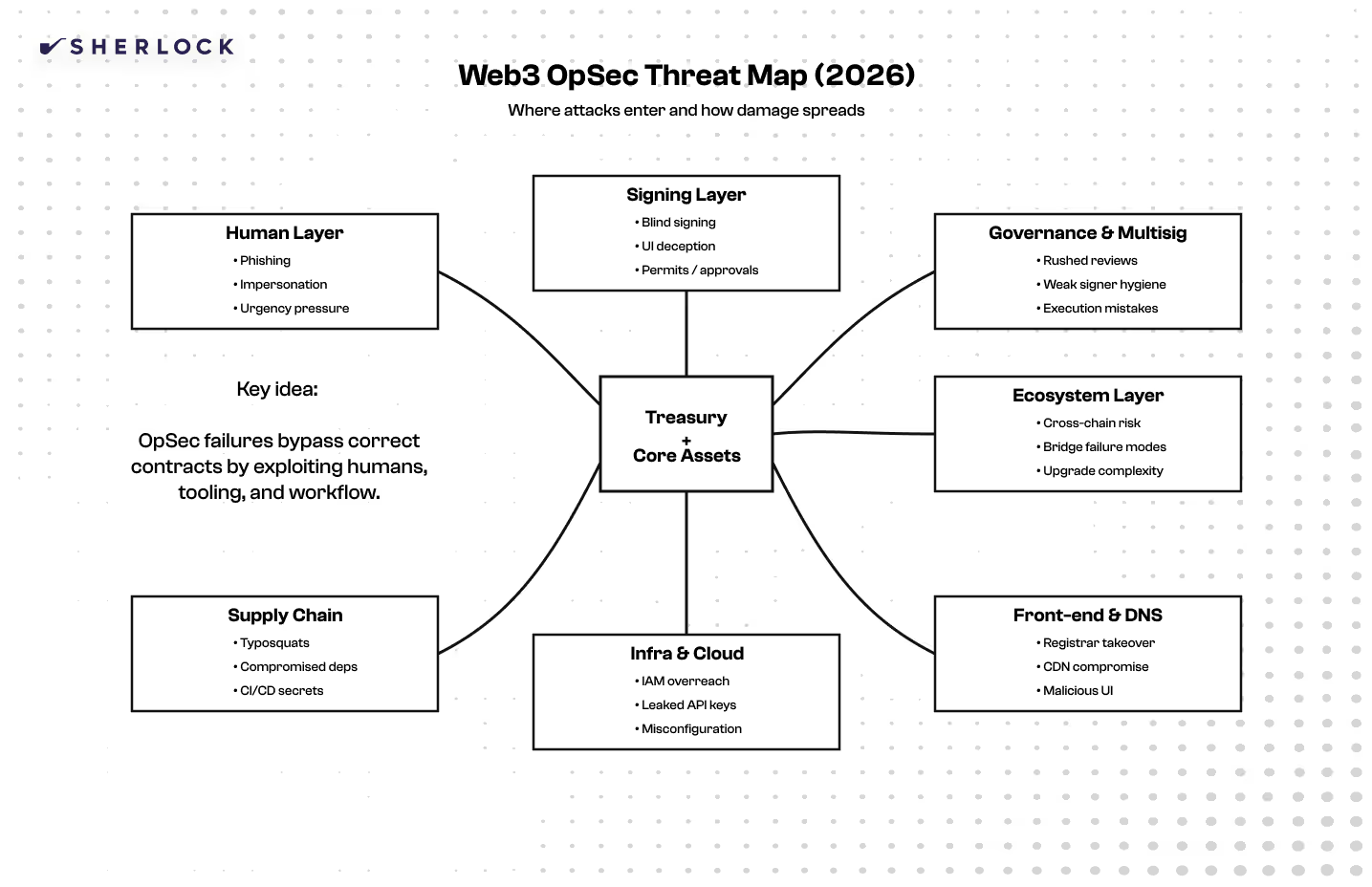
Operational Security (OpSec) is the discipline of protecting the processes and behaviors that determine how systems are operated in the real world. In Web3, OpSec sits above the contract layer and focuses on what happens before, during, and after transactions are signed, upgrades are executed, and infrastructure changes are deployed. It’s the difference between “the code is correct” and “the system is safe.” Strong OpSec reduces the probability that an attacker can bypass technical controls by manipulating humans, tooling, or workflow.
Why OpSec Is Paramount In 2026
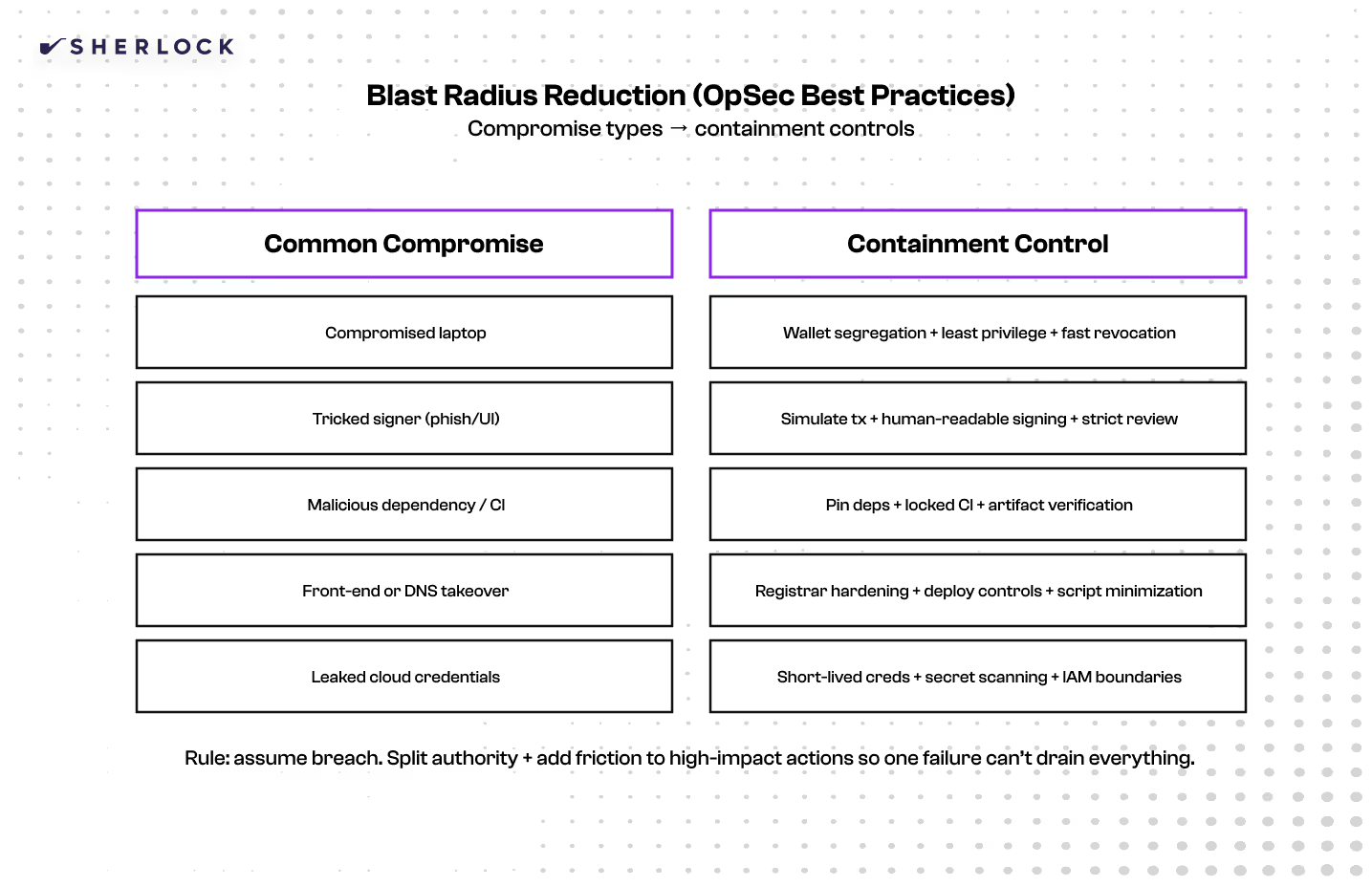
The most effective security teams in Web3 don’t assume they can prevent every exploit. They assume something will eventually fail, and they design the system so that failure is containable. A strong system can survive a compromised laptop, a tricked signer, a malicious dependency update, or even a temporary front-end compromise without losing everything. That requires designing authority boundaries, requiring multiple approvals for high-impact actions, and implementing time delays that create room for detection and response.
If a single mistake can drain the entire treasury, the issue is not just technical—it’s operational. In 2026, the teams that survive are the teams that treat OpSec as product quality.
“It might be easier to attack one of your off-chain pieces than your on-chain pieces. And people will always go for the weakest part in your security posture.”
— Shashank Agrawal, Head of Security at Base (Web3 Security Podcast Episode 10)
The Top OpSec Threats In 2026
1) Transaction Signing Attacks (Blind Signing and UI Deception)
In 2026, the easiest way to steal funds is still to trick someone into signing the wrong thing. Attackers weaponize approvals, permits, and unreadable calldata because most users can’t validate transaction intent from a wallet prompt. This gets worse when the UI is compromised or intentionally misleading, because the user believes they’re confirming something safe while authorizing something permanent. The fix is straightforward but non-negotiable: treat signing as critical infrastructure, reduce allowances, use human-readable signing where possible, simulate transactions before execution, and separate wallets so a single signature can’t become a total loss.
Example: Bybit “Safe wallet interface manipulation” (February 2025)
A major case where signers were shown one thing, but approved another. NCC Group’s analysis describes how attackers compromised the approval process by altering what signers saw in the Safe web interface, leading to catastrophic loss.
2) Social Engineering and Targeted Phishing of Key Operators
Most Web3 breaches begin with a message, not malware. Attackers target founders, multisig signers, and DevOps operators because compromising one privileged identity can bypass millions in security engineering. The tactics are polished: fake calls, impersonated partners, OAuth token theft, and “urgent” escalation pressure. Defense comes from hardened identity and strict verification habits: hardware-key MFA everywhere, no SMS 2FA, limited admin access, and a culture where sensitive requests are confirmed out-of-band and suspicious activity is reported fast.
3) Private Key and Seed Phrase Exposure
Key compromise remains the most preventable catastrophe in crypto. Teams still lose assets because seed phrases end up in screenshots, cloud notes, ticket threads, or browser extensions running on everyday machines. Once an attacker has signing authority, the chain will happily execute theft with perfect reliability. Strong OpSec means hardware wallets for any privileged role, zero digital seed storage, strict separation between browsing and signing environments, least-privilege permissions for deploy and admin actions, and aggressive access revocation when people or responsibilities change.
4) Multisig Failures and Governance Execution Risk
Multisigs and governance reduce single points of failure—until process breakdowns turn them into attack surfaces. Many teams end up with “paper decentralization,” where only a few signers are active, reviews are rushed, and transactions get approved without fully understanding the destination, calldata, or downstream impact. Governance execution adds pressure and complexity, especially during upgrades and emergencies, which is exactly when attackers strike. The fix is execution discipline: realistic signer sets, distributed signer security, repeatable transaction review, timelocks on upgrades, and a break-glass process that’s rare, auditable, and tightly constrained.
Example: Radiant Capital multisig compromise (October 2024)
Radiant’s incident is widely discussed as a multisig security failure where attacker control of signers enabled treasury-draining actions. It’s a strong example of how multisig safety collapses if signer security collapses.
5) Supply Chain Attacks (Dependencies and CI/CD)
The fastest way into a Web3 company is through the tooling it trusts. Typosquatted packages, compromised dependencies, risky GitHub actions, and leaky CI secrets can turn a routine build into a backdoored release. Supply chain attacks work because they hide inside normal engineering workflows and inherit trust automatically. Teams should pin dependencies, reduce package sprawl, lock down CI with short-lived credentials, limit deploy permissions, and verify release artifacts so “shipping faster” doesn’t quietly mean “shipping compromised.”
Example: npm supply chain compromise targeting crypto drainers (September 2025)
A major incident where widely-used packages were compromised, and malicious versions were published, with reporting describing wallet/transaction targeting behavior. This maps perfectly to “dependencies as an attack surface.”
6) Front-End and DNS Takeovers
A protocol can have perfect contracts and still get drained through its website. If an attacker takes DNS, a CDN, or a deploy pipeline, they can serve a malicious front-end that routes users into approvals and signatures that look legitimate. This attack is brutal because users trust the official domain and the damage scales instantly. The defense is to treat the front-end like a financial system: harden registrar access with hardware keys, monitor DNS and certificate changes, restrict deploys, reduce third-party scripts, and assume the UI is a security boundary—not a marketing layer.
7) Cross-Chain and Bridge Risk
Cross-chain systems remain high-risk because they combine large pooled value with complex assumptions about validation, finality, upgrades, and message integrity. When something fails, it often fails across ecosystems, and the blast radius can be extreme. Even strong designs can collapse under operational mistakes, weak monitoring, or bad upgrade execution. The right goal is containment: cap withdrawals, rate-limit flows, isolate permissions, harden message validation, and design with the expectation that cross-chain components will fail eventually.
8) Misconfiguration and Cloud Credential Leakage
Web3 runs on Web2 infrastructure, and attackers know it. Exposed admin dashboards, over-permissive IAM roles, leaked API keys, open buckets, and insecure RPC endpoints routinely become the entry point for larger compromises. These incidents rarely look sophisticated—they look like overlooked hygiene. The fix is disciplined operational engineering: secrets never in repos, continuous secret scanning, least-privilege cloud access, strong admin MFA, restricted endpoints, and monitoring that catches high-impact changes before they become irreversible.
OpSec Best Practices for Web3 Teams in 2026
The best OpSec programs are built around one idea: reduce blast radius. Split authority across wallets and roles so a single compromise can’t drain everything. Harden identity so privileged access isn’t one phish away. Lock down CI/CD and dependencies so your own tooling can’t betray you. Use timelocks and structured review so upgrades and treasury actions don’t rely on trust or urgency. And monitor the few actions that matter most: permission changes, upgrades, high-value transfers, DNS updates, and deployment events.
Final Thoughts: Lifecycle Security Wins in Web3 and Sherlock Helps Teams Build It
Most Web3 security failures don’t happen because a team “forgot to audit.” They happen because security wasn’t treated as a full lifecycle responsibility. A protocol might ship with strong contracts, then drift into risk through upgrades, new dependencies, front-end changes, governance execution, signer turnover, and infrastructure updates. In 2026, the real security is the ability to stay secure as the system evolves.
That’s where Sherlock fits. Sherlock supports teams across the entire security lifecycle: from development, to launch hardening, to post-launch monitoring and response readiness. Instead of treating security as a gate at the end of the process, Sherlock helps make it a continuous discipline built into shipping, operations, and execution. The result is a protocol that doesn’t just look secure at launch, but remains resilient through change when attackers are most likely to strike.
FAQs: Web3 OpSec in 2026
What is the biggest Web3 security threat in 2026?
The most common threat is still credential compromise, leading to malicious signing. This often happens through phishing, front-end compromise, or unsafe approvals.
Are smart contract audits enough?
No. Audits reduce vulnerabilities in contract logic, but many losses happen through OpSec failures, like compromised keys, DNS hijacks, or governance execution mistakes.
What should Web3 teams prioritize first?
Start with:
- Hardware-key MFA everywhere
- Hardware wallets for key roles
- Strict multisig review + timelocks
- Hardened CI/CD and secret handling
- Monitoring for critical changes


