What is Fuzzing in Web3 Security? A High Level Overview
A clear explanation of fuzzing in Web3 security: how it works, why it catches real DeFi vulnerabilities, and where it fits in a modern lifecycle security model.

Fuzzing in Web3 security is a method where software automatically sends tons of different, unpredictable inputs and transaction sequences into a smart contract to see how it behaves. The goal is to catch bugs or vulnerabilities that only appear under weird, unexpected conditions that normal tests never try.
What is Fuzzing In Web3 Security? A High Level Overview
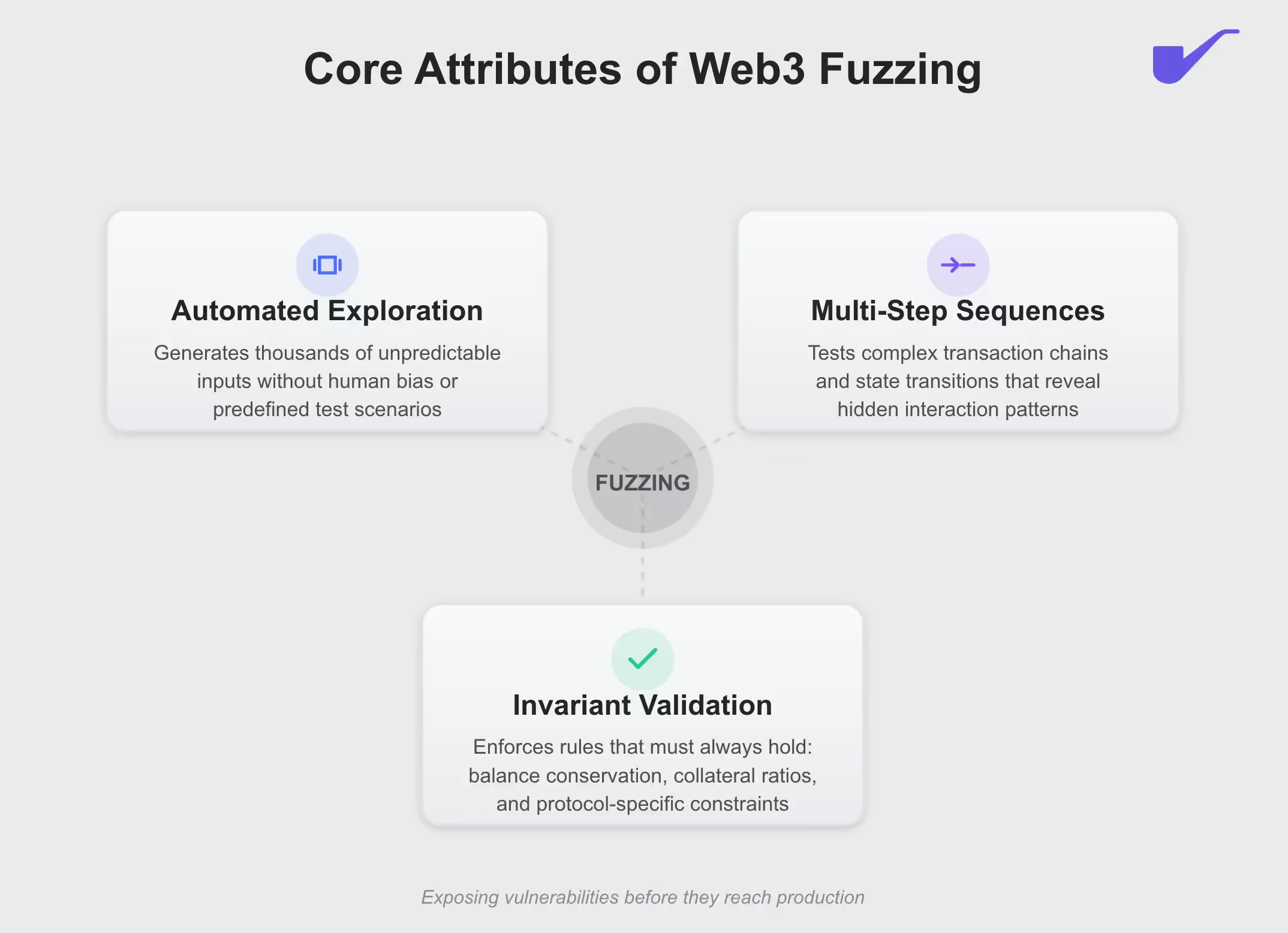
In our experience at Sherlock, fuzzing has become one of the most reliable ways to pressure-test a protocol before real money is on the line. Web3 teams use a mix of approaches to find vulnerabilities: manual auditing, AI auditing, formal verification, researcher contests, and invariant testing... but fuzzing plays a unique role because it doesn’t rely on human intuition or predefined scenarios. Instead, it forces the protocol to confront thousands of unpredictable inputs and transaction sequences, revealing issues that only show up when the system is stressed in strange, unexpected ways.
This matters because most major DeFi failures don’t come from simple “call X with a bad value” mistakes. They emerge from edge-case math, order-dependent behavior, liquidity imbalances, incorrect assumptions about oracles, or multi-step chains that no developer intended. Fuzzing is built to uncover exactly these kinds of hidden paths. By endlessly mutating calls, parameters, and sequences, fuzzers expose the fragile corners of a protocol—the places where accounting breaks, invariants crack, or an attacker could pull value out without triggering an obvious error.
Why Fuzzing Matters More in Web3 Than Anywhere Else
Fuzzing, at an abstract level, is automated experimentation. Instead of a developer choosing a handful of test cases, a fuzzer generates thousands of unpredictable inputs, sequences, and edge-case conditions to see how a smart contract reacts. It’s a way of asking, “What happens if someone interacts with this system in ways we never thought about?” and letting software explore the entire behavioral space without human bias. This makes it valuable in Web3, where protocols are immutable, interconnected, and handle real economic value.
In practical terms, fuzzing becomes a machine-driven attacker simulation. It mutates calldata, alters transaction order, changes msg.sender identities, varies token flows, and chains actions together to uncover strange states that normal testing never reaches. When the protocol hits an unexpected outcome (incorrect balances, broken math, skipped checks, or value drifting somewhere it shouldn’t) the fuzzer flags it. These findings often expose logic errors, financial vulnerabilities, or hard-to-reproduce bugs long before they can be exploited on-chain.
Where fuzzing shows up in real protocol testing:
- Stress-testing financial invariants (AMM curves, collateral ratios, interest calculations).
- Generating multi-step attack sequences that mirror real DeFi exploit patterns.
- Uncovering hidden edge cases in state transitions, accounting, and access control.
How Security Teams Actually Use Fuzzing
Fuzzing isn’t one thing in 2026. There are several forms - property-based fuzzing, stateful transaction-sequence fuzzing, invariant fuzzing, EVM-level fuzzing, and even fuzzing at the client or bridge layer. Each serves a different purpose. Some are designed to test financial math, others focus on exploring deep state transitions, and others push the limits of how the EVM itself handles inputs. Modern security teams combine these approaches depending on what the protocol does and where the risk sits.
Here are some of the most common forms of fuzzing in Web3 security:
1. Writing Invariants That Describe “Correct” Behavior
Researchers start by defining the rules a protocol must always follow: balances must add up, collateral ratios must stay within bounds, certain state changes can only happen under specific conditions, and so on. These invariants become the targets for the fuzzer. If any input or transaction sequence breaks them, the fuzzer immediately flags it. This is the core of how fuzzing produces meaningful findings instead of noise.
2. Letting the Fuzzer Mutate Multi-Step Interactions
Auditors configure fuzzers to generate sequences of calls, not just single inputs. For example: deposit → borrow → repay → borrow again → liquidate. The fuzzer mutates the order, parameters, and caller identities to see which combinations push the system into unintended states. This is how researchers uncover hidden interactions that only appear when several pieces of logic run back-to-back.
3. Running Fuzzers Against Realistic State Snapshots
For complex protocols, teams run fuzzers on forked mainnet states or instrumented EVM environments. This gives the fuzzer real liquidity levels, real debt positions, and real balances to test against. It often surfaces issues that won’t show up on a clean local deployment—like rounding drift, stale oracle assumptions, or inconsistent accounting across different pools or modules.
How to Start Using Fuzzing on Your Own Protocol
Getting value from fuzzing doesn’t require a full security team or months of setup. The fastest path is to take the tests you already have, add a few clear invariants, and let a fuzzer hammer them. For most Solidity teams, this starts in the same place as normal testing: your Foundry or Hardhat test suite. Once you define what “must always be true” for balances, shares, and permissions, fuzzing becomes a way to constantly check those assumptions under strange inputs and call sequences.
From there, you can expand into more advanced setups as the protocol grows. That usually means letting the fuzzer generate multi-step flows, running against forked mainnet state, and wiring fuzzing runs into CI so every code change gets stress-tested automatically. The important part is to start small, wire in invariants early, and keep iterating as your protocol logic and TVL increase.
Simple way to get started:
- Add fuzz tests to existing unit tests (e.g., Foundry @forge fuzzing for function arguments).
- Define 3–5 invariants for your core contracts (supply, conservation of value, access control) and run a property-based fuzzer against them.
- For higher TVL or complex protocols, set up a forked-mainnet fuzz harness for at least one core flow (e.g., deposit → borrow → liquidate) and run it on every major upgrade.
Closing thoughts
Fuzzing has turned into one of the simplest ways to uncover deep, unexpected issues in smart contracts without guessing where the problems might be. It gives teams a way to pressure-test assumptions, catch subtle logic flaws, and validate how their protocol behaves under strange or extreme conditions - long before those conditions appear on-chain.
Regardless of whether you’re a small project adding a handful of invariants to your test suite or a mature protocol running multi-step fuzzing on forked mainnet states, the value is the same: fuzzing exposes the parts of your system you didn’t realize could break. And in a space where immutability and real capital make mistakes expensive, this type of stress-testing is quickly becoming a default requirement for safe deployment.
If you are looking for a full-stack Web3 security partner to help you secure your smart contract code, contact Sherlock today to learn about our lifecycle security model.


