Smart Contract Audit Cost in 2025: What You’re Actually Paying For
Smart contract audits in 2025 range from $8K to $300K+. Learn what drives pricing, how long audits take, and what those costs actually cover.

Smart contract audits in 2026 range from $8,000 to over $300,000, though most protocols pay between $15,000 and $40,000 for a standard pre-launch review. Costs scale with complexity, team size, and the depth of analysis required to secure live onchain code.
Smart Contract Audit Cost in 2025: What You’re Actually Paying For
Auditing in Web3 has become standard practice for any serious Web3 team, but pricing remains widely misunderstood. In 2026, smart contract audits range from around $8,000 for basic token contracts to $300,000 or more for large, interconnected systems. Those numbers reflect differences in scope, depth, and the skill level of the auditors involved.
This article explains what you’re actually paying for. We will go into how cost is determined, what influences it most, and how to tell whether an audit quote matches the work being delivered. Lets get a clearer view of smart contract audit costs in 2026.
What a Smart Contract Audit Actually Covers
A smart contract audit is a structured review of your codebase to identify vulnerabilities before they reach mainnet. It combines automated analysis with manual inspection to uncover logic errors, security flaws, and integration risks that automated tools alone miss. Most audits include a fix-review stage, where auditors confirm that reported issues were resolved and no new ones were introduced.
How often teams audit depends on how quickly the code changes and the value at stake once it’s live. Protocols handling user funds or deploying complex systems often commission multiple rounds of audits from different providers before launch. Each team approaches the code differently, increasing the likelihood that independent reviewers catch what others might miss. The frequency of auditing is driven by code churn, risk exposure, and the need for independent validation before capital goes onchain (and subsequently at risk of exploit).
Larger projects sometimes layer an internal security review, a private audit, and a contest-based audit in sequence to cover depth, breadth, and adversarial testing. Smaller teams might opt for a single pre-launch audit, then rely on ongoing bug bounties or monitoring after deployment.
Different Auditing Models and How They Work
Smart contract audits generally fall into two broad categories: fixed-team audits and dynamically sourced audits.
Fixed-team audits are what most people picture when they think of a traditional security review. A single firm assigns a small, consistent group of in-house auditors to examine a codebase over a set timeframe. Pricing is usually based on hourly or weekly rates tied to the team’s size and experience. The benefit is continuity (auditors gain a deep understanding of the project’s architecture) but the trade-off is coverage, since a limited number of reviewers can only apply so many perspectives and attack methods. This is the auditing model provided by firms like Halborn.
Dynamically sourced audits expand that model by drawing from a larger network of vetted researchers. Instead of assigning whoever is available, these audits match specialists to the protocol’s language, complexity, and risk profile. Costs are determined by scope and the seniority mix of the selected researchers rather than a flat rate per week. Sherlock’s collaborative audit model follows this structure... Each engagement is assembled from the best-qualified talent in its network. This approach increases coverage, reduces blind spots, and allows teams to pay for depth that directly aligns with the code they’re shipping.
Collaborative Audits vs. Audit Contests
It’s important to note the distinction between collaborative audits and audit contests, since they differ in both structure and cost.
A collaborative audit engages a focused team of senior researchers who work together on the same codebase: sharing insights, cross-reviewing findings, and concentrating on architectural depth. Pricing is usually a fixed quote based on scope, timelines, and the experience level of the auditors. This article primarily focuses on collaborative audits.
Audit contests, by contrast, open the code to a wider network of independent researchers who compete for payouts. The project team funds a prize pool to be paid out contingent on the level of vulnerabilities uncovered, which is then distributed among researchers based on the severity of the issues they uncover. This model shifts cost from hourly labor to results: teams pay only for validated findings rather than time spent. Many protocols use both models before launch: the collaborative audit delivers structured assurance and detailed remediation guidance, while the contest applies broad, creative pressure testing at volume.
How Smart Contract Audit Costs Break Down
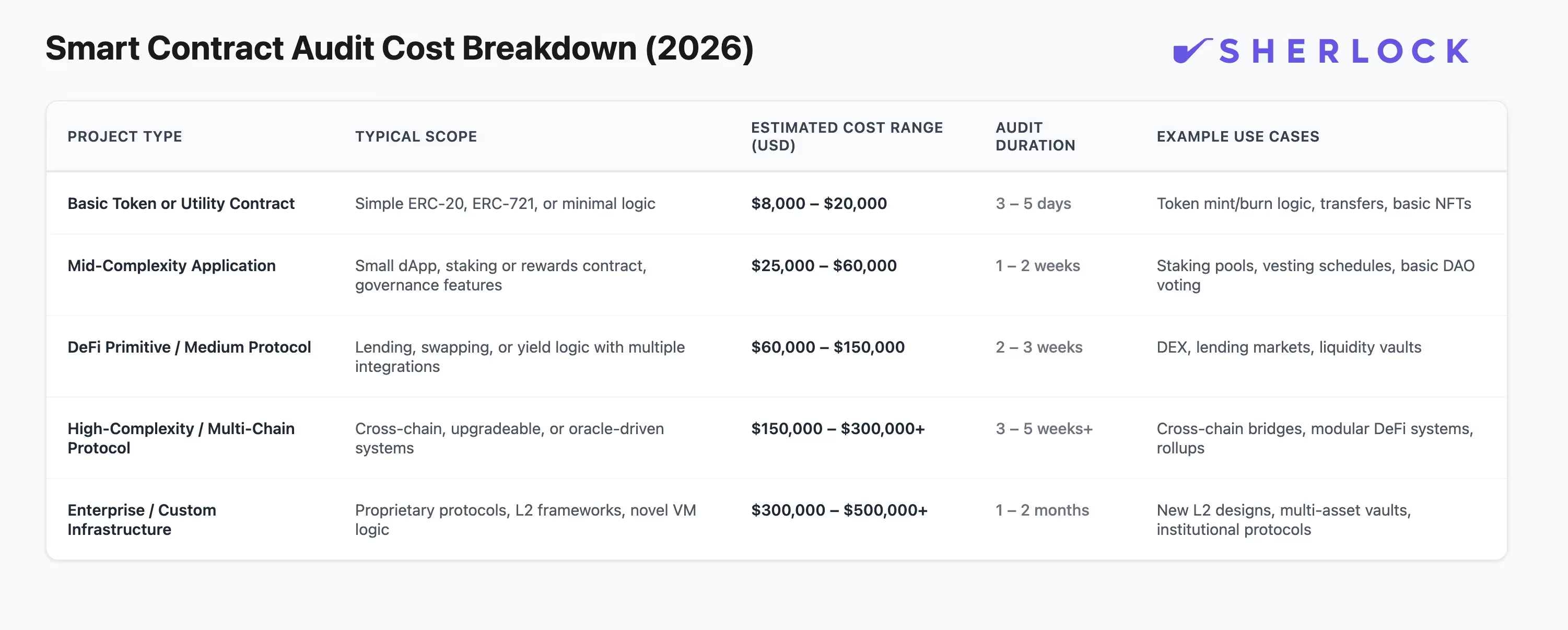
Audit pricing in 2026 spans a wide range, often from around $8,000 for simple token contracts to $300,000+ for complex, multi-chain systems. The spread reflects how different projects demand different levels of analysis, team size, and testing methodology. A basic ERC-20 audit might take under a week and involve one or two reviewers, while a high-complexity DeFi protocol could require a multi-week effort with multiple senior auditors, specialized tooling, and iterative fix reviews.
The cost of an audit depends on several core variables that compound as complexity increases:
- Codebase size and complexity: Larger, interconnected systems take longer to review and require deeper architectural understanding.
- Security model and integrations: Cross-chain logic, oracles, and composable DeFi protocols introduce more attack surfaces.
- Audit type and scope: Collaborative audits and contests differ in structure and pricing—some charge fixed project fees, others fund prize pools.
- Auditor experience: Senior, high-demand researchers and firms command higher rates but bring stronger analysis and remediation guidance.
- Timeline and readiness: Rushed audits, limited documentation, or ongoing code changes increase review time and drive cost upward.
These factors often intersect. For example, a mid-sized DeFi protocol integrating multiple third-party libraries might start with a $60K collaborative audit quote. If the team updates the code mid-audit or requests a follow-up contest for extra coverage, total costs can climb past $100K. In contrast, a simple staking contract with clean documentation and no dependencies might close for under $20K. The difference reflects how risk, depth, and required expertise scale together as systems grow more complex.
The Key to Budgeting Effectively for a Smart Contract Audit
The best way to budget for an audit is to start from scope, not price. Map out how much of your codebase needs review, what stage it’s in, and how critical it will be once deployed. From there, get quotes from multiple providers with different structures—one traditional audit firm, one collaborative network, and, if relevant, a contest-based model. Each will approach your code differently, and pricing reflects that. Some teams use one provider for architectural review and another for independent validation before mainnet. This approach costs more upfront but offers stronger coverage and credibility with investors and users.
If your code will handle value onchain, plan security spending as a lifecycle budget rather than a one-off event. Set aside funds for a pre-launch audit, a follow-up audit or contest after major fixes, and post-launch protection through a bug bounty or financial coverage program. A good rule of thumb: allocate 5–10% of total funds at risk toward ongoing security. It’s easier to scale protection than to recover from an exploit.
Sherlock’s Recommendations for Audit Spending
- Start vetting auditors 3–4 months before launch.
The best auditors and contest slots book early. Begin outreach when core contracts are 70–80% complete so you can coordinate timelines and code freezes. Expect high-demand providers to have a 6–8 week lead time. - Plan for at least two audit passes before mainnet.
One for structural review and another to validate fixes or major updates. Most high-value protocols budget for two separate engagements—either two providers or one audit plus a contest—for redundancy and broader coverage. - Reserve 10–20% of your security budget for post-launch protection.
Live bug bounties and coverage programs close the window between deployment and exploitation. Teams that skip this layer end up paying far more in loss response than prevention.
Conclusion
Security is tantamount in Web3 because every contract deployed carries real financial risk. The cost of an audit reflects that exposure: teams are paying for time, expertise, and accountability from people who understand how code can fail under pressure. With user funds on the line, auditing becomes a foundational part of the development process, not a post-launch formality. The spend may seem high, but it’s a fraction of what a single exploit can cost a protocol.
Reach out to Sherlock to get clear guidance on pricing, timelines, and how to structure your audit plan.
F.A.Q.
1. How early should teams book a smart contract audit?
Most reputable auditors book out 6–8 weeks in advance. Teams should start outreach 3–4 months before launch to align timelines, finalize code freezes, and avoid last-minute pricing premiums.
2. How do I decide between a collaborative audit and an audit contest?
Collaborative audits are structured and deep—ideal for complex systems that need coordinated review. Contests apply scale and creative testing by opening the code to a larger network. Many teams use both: a collaborative audit for depth and a contest to pressure-test coverage before launch.
3. How long does a typical audit take?
Short audits for basic contracts take about a week. Complex DeFi or multi-chain systems can require 3–5 weeks or longer, depending on code size, dependencies, and the number of fix-review cycles.
4. Is one audit enough before launch?
Usually not. Teams handling user funds should plan for at least two rounds of review... either two providers or one audit plus a contest. Each round adds new perspectives and reduces blind spots.
5. What happens after an audit is complete?
Post-audit protection continues through bug bounties, on-chain monitoring, and financial coverage. Smart teams treat the audit as the start of an ongoing security cycle, not the finish line.


.png)