5 Steps to Becoming a Top-Level Smart Contract Auditor
A proven, five-step blueprint from Sherlock’s top auditors on how to start earning money as a smart contract auditor in under a month. Learn how to master codebases, build your checklist, think like an attacker, and accelerate your growth through fast feedback.

So you’ve decided you want to be a smart contract auditor, now what?
Today, we are answering one of the most common questions our top researchers at Sherlock get asked: how did you get started?
This article will serve as your guide not only to get started, but also to continuously improve your skills until you find your name at the top of the Sherlock leaderboard.
We cannot guarantee results. There is no shortcut for hard work, especially in the audit game. But we can give you the blueprint to success. This blueprint isn’t something we came up with ourselves. This is a blueprint that comes directly from the top researchers on the Sherlock leaderboard and the founding members of Blackthorn. They’ve put in the hours and earned their place as the best researchers in the world. Now you can learn from the best.
Prerequisites: The Technical Foundation You Need
Smart contract auditing is not an entry-level activity. It takes a working knowledge of smart contract development, among other skills. If you are completely new to web3 and smart contract development, we recommend you start with these steps:
- Learning basic blockchain and EVM concepts
- Studying Solidity and smart contracts
- Learning Foundry
For this article, we are going to assume that you are an intermediate-level or higher smart contract developer.
Step 1: Understand Codebases Deeply
This sounds obvious, but we cannot stress enough how important it is to understand a codebase fully before trying to audit it. This is the most time-consuming step in our guide; there is no substitute for putting in the hours. Our top auditors agree—this is a must.

So what does this mean in practice?
We recommend choosing 1 or 2 types of protocols and spending a few days going deep into the codebases of each. Ideally, these would be both well-known protocols and protocols that have an upcoming contest or a live bug bounty. This way, if you do find something as you are getting started, you can make some money in your first month.
Top Researcher Pro Tip: Pick protocols you are interested in. You are not going to survive long if you are not interested in the type of protocol you are looking at, and if you are not curious about the codebase.
For example, if you are interested in lending protocols, dive deep into Aave. If you are interested in AMMs, dive deep into Uniswap.
How can I tell if I truly understand a codebase?
There’s no one way to know, or a specific benchmark to pass. There will be signs, but you need to put in the hours first. Top researchers can conceptualize vulnerabilities even when they aren’t looking directly at the code because they understand the protocol. You want to reach a point where you can visualize a codebase in your head without even looking at it.
One way to get there is to practice implementing a protocol from scratch. If you are interested in lending protocols, try building one that works. This will help you understand the functionalities more deeply than just reading what others have written.
Once you fully understand a codebase, you can already start finding issues. But that’s just the beginning.
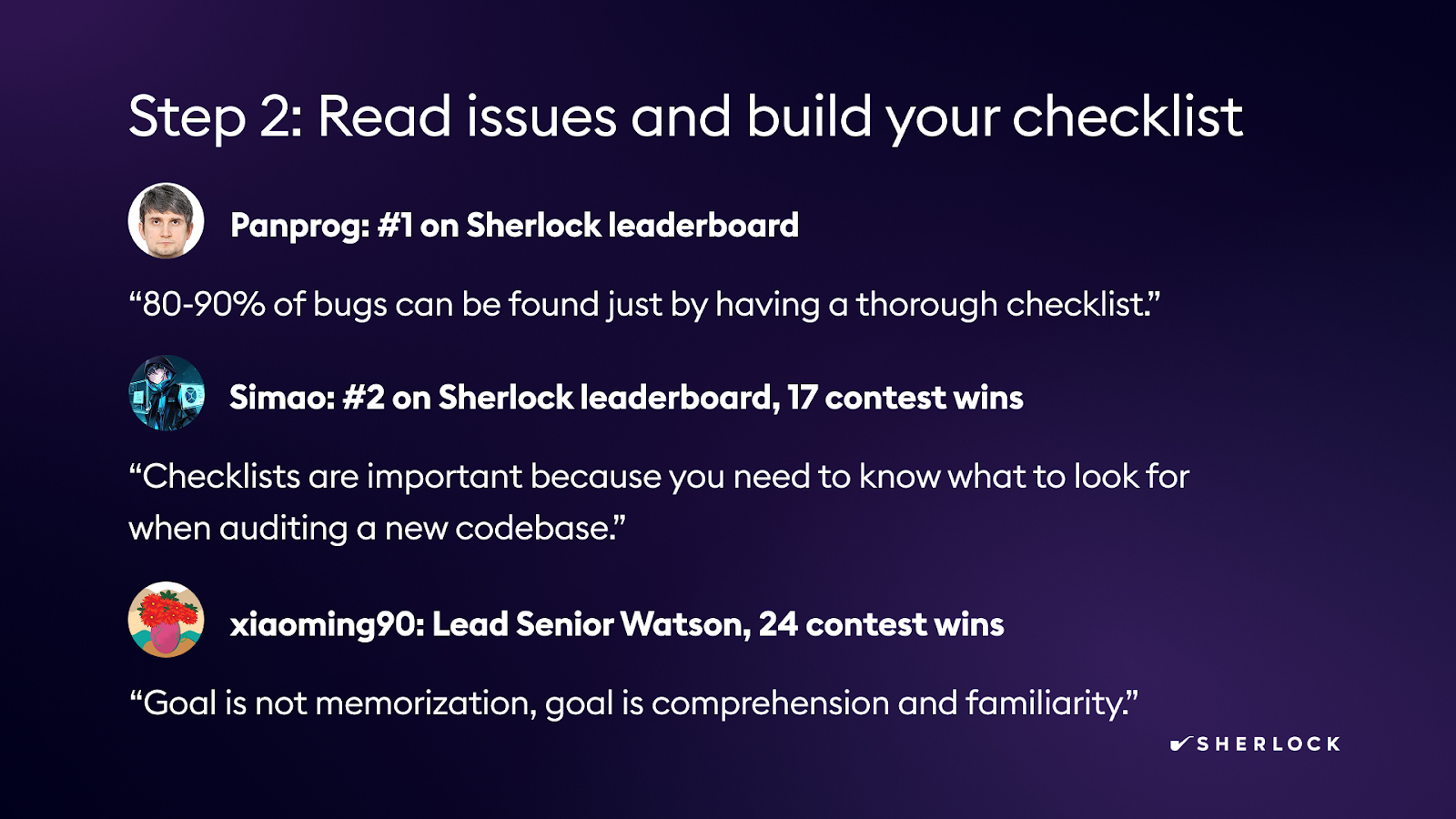
Step 2: Read Issues and Build Your Checklist
Now that you understand the codebase, it’s time to start auditing. But first, we need to look at where issues have been found in the codebase. This should give you an idea of what the attack paths are for this type of protocol. There are a lot of patterns, so it’s important to understand those past patterns before trying to come up with them yourself.
Where to read past issues
It’s beneficial to read through as many issues in the codebase you have chosen as you can. Here’s where you can find them:
- Audit contest results
- Collaborative audit reports
- Bug bounty writeups
Great, now you understand your codebase deeply, and you understand the issues that have already been reported in that codebase.
Building checklists
There are many checklists available, but we believe it’s essential to create your own, ensuring you understand all its contents. Begin by categorizing all issues you encounter into vulnerability types and patterns. These patterns will give you structure to categorize your checklist issues, and the common categories will provide you with a better chance at finding a similar vulnerability in the future. It’s important not to add issues to the checklist that you don’t understand.
A well-constructed checklist that you truly understand will give you a significant advantage over the competition. But don’t just take our word for it; here are some of our top researchers’ takes:
Step 3: Adopt the Attacker’s Mindset
Now that you understand the codebase and the issues, and you have your checklist, it's time to walk the walk. Most smart contract developers aren't trained in the attacker's mindset. If you are a developer, you are always trying to find ways to make things work; you are a builder. That's great, but that mindset can hold you back as an auditor.
Instead, you need to change your mindset to become an attacker. Now you need to find all the ways to break something, to make sure it doesn’t work.
It’s about finding loopholes, even figuring out how to cheat is a good mindset. Make no assumptions; assume nothing is implemented securely and everything can be broken.
This is a significant reason the audit industry in Web3 exists—it can be very difficult for protocol builders to shift their mindset and try to break what they've just built.
How do I develop an attacker’s mindset?
The first step is to do basic CTFs like Ethernaut or Damn Vulnerable DeFi. These are simpler, but will help you get into the mindset of being an attacker instead of a builder.
Another thing you can do is to read reports of critical vulnerabilities, issues that really cause a protocol to lose its functionality. Audit and bug bounty reports are good here, but exploit reports and post-mortems are even better.
Again, don’t just take our word for it. This is advice from real researchers who’ve had real success on Sherlock.

Step 4: Get Hands-on Experience
As important as steps 1-3 are, the real learning comes from hands-on auditing. We want you to get to auditing as fast as you can. That doesn’t mean skip steps 1-3.
DO NOT skip steps 1-3.
But there’s no way to become a top-tier auditor without actually auditing.
Where do I start?
This part is contentious. Some say to start with larger contests, but we think repetition is more important. Start with short contests to get more reps. As soon as you believe you can't find anything else in the codebase, move on to the next.
Here’s your priority list for how to get your first hands-on experience:
- Audit contests
- Shadow audits (shadow a more experienced researcher during an audit)
- Bug bounties (this can be demoralizing, because your chances of finding something are lower, but it can also be more lucrative)
Don’t forget, choose contests that are similar to protocols you already understand, and use your checklists!
Step 5: Create a Fast Feedback Loop
Every step in this list is essential to becoming a great auditor. Having said that, this is the most important step because it makes learning intentional. This is the real key to improving faster than your peers in auditing.
What do we mean by feedback loop?
Simply, fail fast. Go through contests quickly, see what you missed and why you missed the issues, and repeat. Always check what you missed after a contest, and also why you submitted any invalid issues.
Top Auditor Pro Tip: Get comfortable with failing and learning from your mistakes. The more comfortable you are with this process, the faster you will improve.
This seems like a lot to handle as a beginner, but we promise it is possible. With hard work, you’ll be winning contests in no time at all.
Again, don’t trust us, trust those who have done it. Lead Senior Watson Vinica_boy’s first Sherlock contest was in July 2024, and he won his first contest by January. How’d he do it? Here’s his guide on how to evaluate contest results:
- Why did I miss the issue?
- What question could I have asked myself during the audit to find it?
- What heuristics/patterns could I extract from this issue so I can add it to my checklist for next time?
- How can the issue be mitigated?
Still don’t believe him? Here’s advice from two legends of the audit world:

This is how the best auditors iterate. Every bug missed becomes a lesson that sharpens pattern recognition and decision-making.
The 5 Steps to Becoming a Smart Contract Auditor as Fast as You Possibly Can
To summarize, here’s your step-by-step path to becoming a smart contract auditor according to the best researchers in the world:
Step 1: Understand Codebases Deeply
Step 2: Read Issues and Build Your Checklist
Step 3: Adopt the Attacker’s Mindset
Step 4: Get Hands-on Experience
Step 5: Create a Fast Feedback Loop
If you’d like to see these steps brought to life, our CEO, Jack Sanford, recently presented this guide at EthCC.
You now have everything you need to become a successful auditor, and we can’t wait to see your name at the top of the leaderboard.
Sherlock
Sherlock was founded on a simple belief: security must evolve alongside the code it protects. By uniting audits, contests, bounties, and coverage into one model, Sherlock delivers protection that adapts as protocols build, launch, and grow.
To work with the world’s best security researchers, like the ones who helped develop this guide, reach out below.


